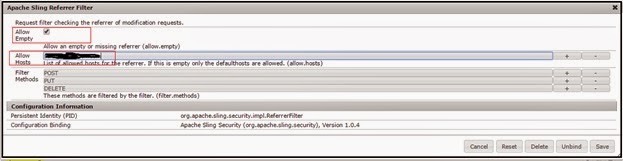
Expand Apache Sling Referrer Filter
Add the SAML SSO server hostname to the Allowed Hosts section (depending on the authoring environment you are configuring), Check the Allow Empty checkbox and Click Save.
Configure Adobe Granite SAML 2.0 Authentication Handler:Configured the required details for authentication
Path
|
/
|
Service Ranking
|
5002
|
IPD URL
|
https://host/SAML2/sso/SAML2Service - URL of the IDP where the SAML Authentication Request should be sent to
|
IDP HTTP Redirect
|
Unchecked - Use an HTTP Redirect to the IDP URL instead of sending an AuthnRequest-message to request credential
|
Service Provider Entity ID
|
http://dev-author.com/ - ID which uniquely identifies this service provider with the identity provider
|
Default Redirect
|
/
|
User ID Attribute
|
UserID - The name of the attribute containing the user ID used to authenticate and create the user in the CRX repository
|
Use Encryption
|
Unchecked - Whether or not this authentication handler expects encrypted SAML assertions
|
Autocreate CRX Users
|
Unchecked - Whether or not to autocreate nonexisting users in the repository
|
Add to Groups
|
Unchecked - Whether or not a user should be autmatically added to CRX groups after successful authentication
|
Group Membership
|
<empty--no value> - The name of the attribute containing a list of CRX groups this user should be added to
|
NameIDPolicy Format
|
urn:oasis:names:tc:SAML:2.0:nameid-format:unspecified - The value of the NameIDPolicy format parameter to send in the AuthnRequest message.
|
Click Save
Add the SAML certificate:
Log into the Authoring server using ssh.Create a file called /tmp/idp.pem on the Authoring server, and paste the contents of the certificate into the file. Save the file.
e.g.
-----BEGIN CERTIFICATE-----
v0+H34mZVykVp1QmXs6r6xPppTMZ6YbGs8l+RfmMy4pAFphTimiQz/y/eWJCpvo7
Hg+VqF/9Kong61W9ogDbkAsCzWoyQyE1OkzqjLM19N6QDmbGheUQMS70bhiPEagz
…….
-----END CERTIFICATE-----
Run this command to push the certificate into AEM, replacing PASSWORD with the admin password:
curl -u admin:PASSWORD -F idp_cert=\<idp.pem -F idp_cert@TypeHint=Binary http://localhost:4502/etc/key/saml
Browse to the AEM server (http://localhost:4502/)and you should be redirected to the SSO server for authentication and send it to the AEM screen upon successful authentication(http://localhost:4502/)).

No comments:
Post a Comment
If you have any doubts or questions, please let us know.