This post will explain the steps required to protect the published content from anonymous access through SAML based SSO while accessing via dispatcher/publisher - Adobe CQ5/AEM
Out of scope for this post - Configurations of IDP provider. Make sure the return URL configured in SAML provider is /saml_login
Enable Authentication for required content path: Go to http://localhost:4503/system/console/configMgr(publisher)
Search for Apache Sling Authentication Service
Add the path that required the authentication to Authentication requirements in the following format +<<Content Path>> e.g. +/content/test

Configure the IDP certificate in Adobe Experience Manager(AEM): Go to http://localhost:4503/system/console/configMgr(publisher)
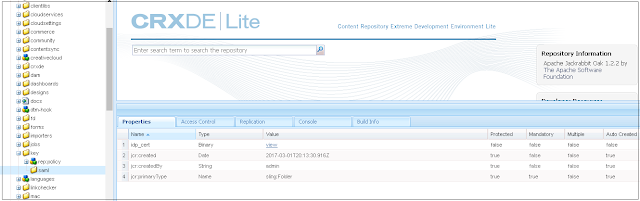
Under /etc/key in the repository, create a node called "saml"(type nt:folder).
Inside this node, add a new binary property called "idp_cert" for the public certificate of the IdP.
Upload the certificate file by double clicking on idp_cert property
Save All
Go to: http://localhost:4503/libs/granite/security/content/useradmin.html(publisher)
Select any user because TrustStore is global to AEM
Create trust store by supplying the password & then manage trust store
Upload the IdP certificate & make note of the certificate Alias
Go to: http://localhost:4503/libs/granite/security/content/useradmin.html(publisher)
Select authentication-service
Create KeyStore by supplying the password
If encrypting SAML assertions then go to manage KeyStore for uploading the private & public key
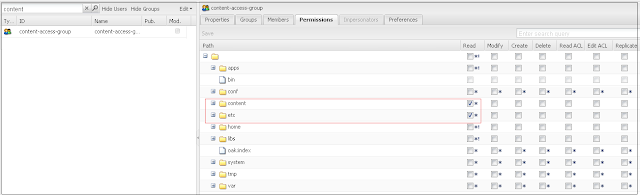
Configure the user group for restricting the access to required content: Go to http://localhost:4503/useradmin(publisher)
Create a new group(content-access-group) with read access to content(provide the read assess only to the specific folder under content -/content/test and the required dam folders) and etc folder
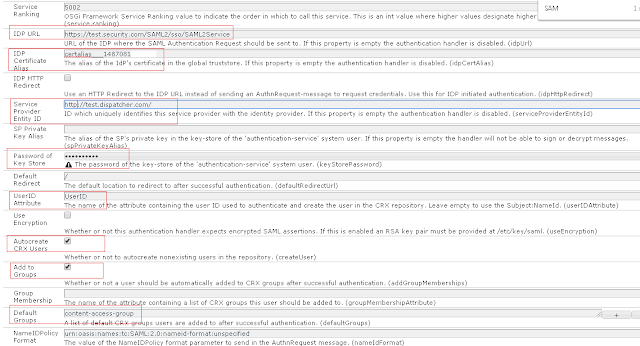
Configure SAML 2.0 Authentication Handler:
Go to http://localhost:4503/system/console/configMgr (publisher)
Search for Adobe Granite SAML 2.0 Authentication Handler
Provide the required details
Search for Adobe Granite SAML 2.0 Authentication Handler
Provide the required details

IDP URL - URL of the IDP where the SAML Authentication Request should be sent to Provide all the required values
Service Provider Entity ID - ID which uniquely identifies this service provider with the identity provider
UserID Attribute - The name of the attribute containing the user ID from IDP
IDP Certificate Alias - Provide the certificate alais created in the above step
Select Auto create CRX Users
Select Add to Groups
Specify content-access-group in Default Groups(group created in previous step)
Password of Key Store - Specify the key store password specified in the above step.
Configure Referrer Filter:
Service Provider Entity ID - ID which uniquely identifies this service provider with the identity provider
UserID Attribute - The name of the attribute containing the user ID from IDP
IDP Certificate Alias - Provide the certificate alais created in the above step
Select Auto create CRX Users
Select Add to Groups
Specify content-access-group in Default Groups(group created in previous step)
Password of Key Store - Specify the key store password specified in the above step.
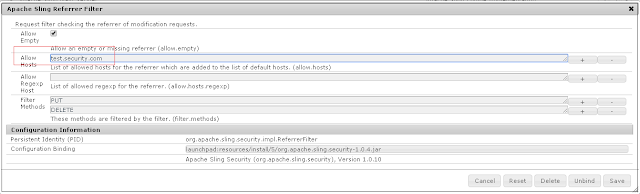
Configure Referrer Filter:
Go to http://localhost:4503/system/console/configMgr(publisher)
Serach for Apache Sling Referrer Filter
Configure IDP host at Allow Hosts
Serach for Apache Sling Referrer Filter
Configure IDP host at Allow Hosts

Access the content URL now - http://test.dispatcher.com/content/test/en.html
The user will be redirected to SAML provider and will be redirected to target page upon successful authentication.
All the user configured in SAML provider will be able to access the target page and the users will be auto created in AEM after successful authentication.
If we want to give them access only to predefined users in AEM then remove Auto create CRX Users and Add to Groups from Adobe Granite SAML 2.0 Authentication Handler configuration.
The authentication will not work if multiple publishers serve the request, as a solution we have to enable the sticky session to make sure the browser sessions are directed to same dispatcher/publisher
The user will be redirected to SAML provider and will be redirected to target page upon successful authentication.
All the user configured in SAML provider will be able to access the target page and the users will be auto created in AEM after successful authentication.
If we want to give them access only to predefined users in AEM then remove Auto create CRX Users and Add to Groups from Adobe Granite SAML 2.0 Authentication Handler configuration.
The authentication will not work if multiple publishers serve the request, as a solution we have to enable the sticky session to make sure the browser sessions are directed to same dispatcher/publisher
No comments:
Post a Comment
If you have any doubts or questions, please let us know.