LDAP (Light Weight Directory Access Protocol) is used for accessing a centralized repository. In some projects, clients maintain a separate LDAP server and prefer to maintain their users at their side.
LDAP is often used to achieve Single Sign-On which allows users to maintain multiple applications after logging in once.
In this article we are going to use below servers:
1) Apache DS 2.0.0 (LDAP Server)
2) AEM 6.4.0
First, let's start with setting up our LDAP server.
Setting Up the LDAP Server
1) Go to the URL http://directory.apache.org and download the Apache Directory Studio 2.0.0-M 14.
2) Install Directory Studio.
3) Right-click on the LDAP Servers and click New --> New Server
4) Click on Apache DS 2.0.0 that comes in the pop-up window.
5) Then Right Click on the server and click on run.
6) Confirm the port number for LDAP Server (Default 10309) and LDAP SSL (Default 10306).
7) Once done you'll be able to see the LDAP Server in the Started state.

8) Now Click on LDAP on top and Click on New Connection.
9) Add the below details in the new connection:
a) Connection Name: LDAP
b) Host Name: localhost
c) Port: 10389
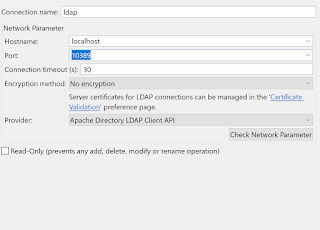
10) Click on Check Network Parameter and you'll get a successful message and click on Next.
11) Add the below properties in the Authentication tab.
Authentication Method: Simple Authentication
Bind DN or user : uid=admin,ou=system
Bind Password: secret (default password)
12) Click on Check Authentication and you'll get a successful message. And then click Finish.
13) Once you click on Finish, you'll get the below structure created:
Adding Users and Groups
1) Right Click on dc=example and dc=com and click on New -> New Entry.
2) In the New Entry wizard, click on Create Entry from Scratch and click on Next.
3) Search the organizationalUnit from the Available Object Classes and click on Add. Click on Next
4) On the RDN field enter ou. Enter the value as 'Groups'.
5) Repeat steps 1-4 for the users. In the RDN field enter ou and value as users.
6) Right-click on ou=users and Click on New-> New Entry.
7) Click on Create entry from scratch and click on Next.
8) Search the inetOrgPerson from the available Object Classes and click on Add.
9) In the RDN field enter cn and value = varun
10) Click on next and Under the sn attribute, enter ‘sharma’ (sn stands for Surname).
11) We need to add two more attributes to this user.
12) Right Click on the Attribute field enter uid. In this attribute enter the value as varun.
13) Similarly add the attribute as userPassword and click on next.
14) You will be asked to enter a password. Enter admin as the new password. Make sure that the Select Hash Method is set to SHA. (For this article we will keep the users in the admin group)
15) Now we will add the users to the group. Right-click on ou=Groups and click New -> New Entry and click Click Entry from Scratch and Click on Next.
16) Search groupOfNames from the Object classes and click on Add.
17) In the RDN field enter cu and enter the value as admin.
18) Now it will ask you to pick up the member field browser to the user varun we created.
19) Click on Finish.
AEM Configuration for LDAP
After the release of AEM 6.0, there are three configurations that need to be done rather than the jaas.conf file which was there in the earlier releases.
1) Apache Jackrabbit Oak LDAP Identity Provider: It defines how users are retrieved from the LDAP server
Go to http://localhost:4502/system/console/configMgr and search for the above configuration and click on the + icon to add a new config. Configure the below properties:
a) LDAP Provider Name -- Name of the provider of LDAP. Enter the value as LDAP.
b) LDAP Server Hostname -- Host Name of Provider. Enter the value as the hostname.
c) LDAP Server Port --- Port of LDAP Server. Enter the value as 10389.
d) Bind DN --- DN that is used of a bind. Enter the value as uid=admin,ou=system
e) Bind Pwd -- Corresponding DN password. Enter the value as a secret.
f) User base DN ---Base DN for user searches, Enter the value as dc=example,dc=com
g) User Id attribute--- the name of user attribute. Enter the value as uid
Note: UID attribute should be a unique value when creating users in the LDAP servers.
2) Apache Jackrabbit Oak Default Sync Handler-
The synchronization handler will define how the Identity Provider users and groups will be synchronized with the repository.
Go to http://localhost:4502/system/console/configMgr and search for the above configuration and click on the + icon to add a new config. Configure the below properties:
a) Synch Handler Name: default
b) User property mapping: profile/nt:primaryType="nt:unstructured" and profile/givenName=cn
c) User Auto Membership: administrators
3) Apache Jackrabbit Oak External Login Module-
This module is used for binding the two modules.
Go to http://localhost:4502/system/console/configMgr and search for the above configuration and click on the + icon to add a new config. Configure the below properties:
a) Identity Provider Name: LDAP
b) Synch Handler: default
Now we have configured all the users we still need to synchronize it to get the users in the AEM.
Synchronize Apache DS Users
1) Go to JMX console (http://localhost:4502/system/console/jmx). Search for External Identity Synchronization Management and click on the row.
2) Click on syncAllExternalUsers() to sync all the users manually.
3) Click the Invoke button.
Debugging LDAP
Add the below loggers in the logger configuration with log level as debug.
1) logs/ldap.log : org.apache.jackrabbit.oak.security.authentication.ldap
2) logs/external.log : org.apache.jackrabbit.oak.spi.security.authentication.external
Source:


No comments:
Post a Comment
If you have any doubts or questions, please let us know.